Information security threats continually evolve, and defenses against them must evolve as well. Many best-practice frameworks, standards and laws require a flexible response based on regular risk assessments. A risk assessment is a key to ensuring an organization is prepared and protected.
An information security risk assessment will give you an accurate snapshot of the security risks that might compromise the confidentiality, integrity and availability of your organization’s information assets. It can be used to help an organization select the appropriate security controls based on business needs and a cost-benefit analysis. ISO/IEC 27001:2013 (ISO 27001) defines best practices for building and managing an information security management system (ISMS), a risk-based approach to securing corporate information assets that addresses people, processes and technology.
Clause 6.1.2 of ISO 27001 explains that the risk assessment process must, among other things, establish and maintain information security risk criteria, ensure that repeated risk assessments product consistent and valid results, and identify risks associated with the loss of the information covered.
Conducting a Successful Risk Assessment
The steps below will help an organization build an effective risk assessment framework.
Define the requirements
A formal methodology is required to establish a transparent and measurable risk assessment framework as mandated by 6.1.2 of ISO 27001, an information security standard published by the International Organization for Standardization and the International Electrotechnical Commission. The methodology and framework also are guided by the ISO 31000, a family of standards relating to risk management codified by the International Organization for Standardization, with the purpose of providing principles and generic guidelines on risk management.
The first step is to identify the business, regulatory and contractual requirements that must be met related to information security. For example, the requirements of the European Union’s General Data Protection Regulation (GDPR) apply to organizations that process or control personal information. The second step is to establish the risk scale, a combination of the likelihood and impact of security incidents. Risk assessments may be qualitative or quantitative. Figure 1 depicts a risk scale.
The risk appetite is the result of an analysis of the risks and determining how to respond to them. Events that are highly unlikely to happen or are highly unlikely to disrupt the organization if they do happen might be ones that management is prepared to tolerate.
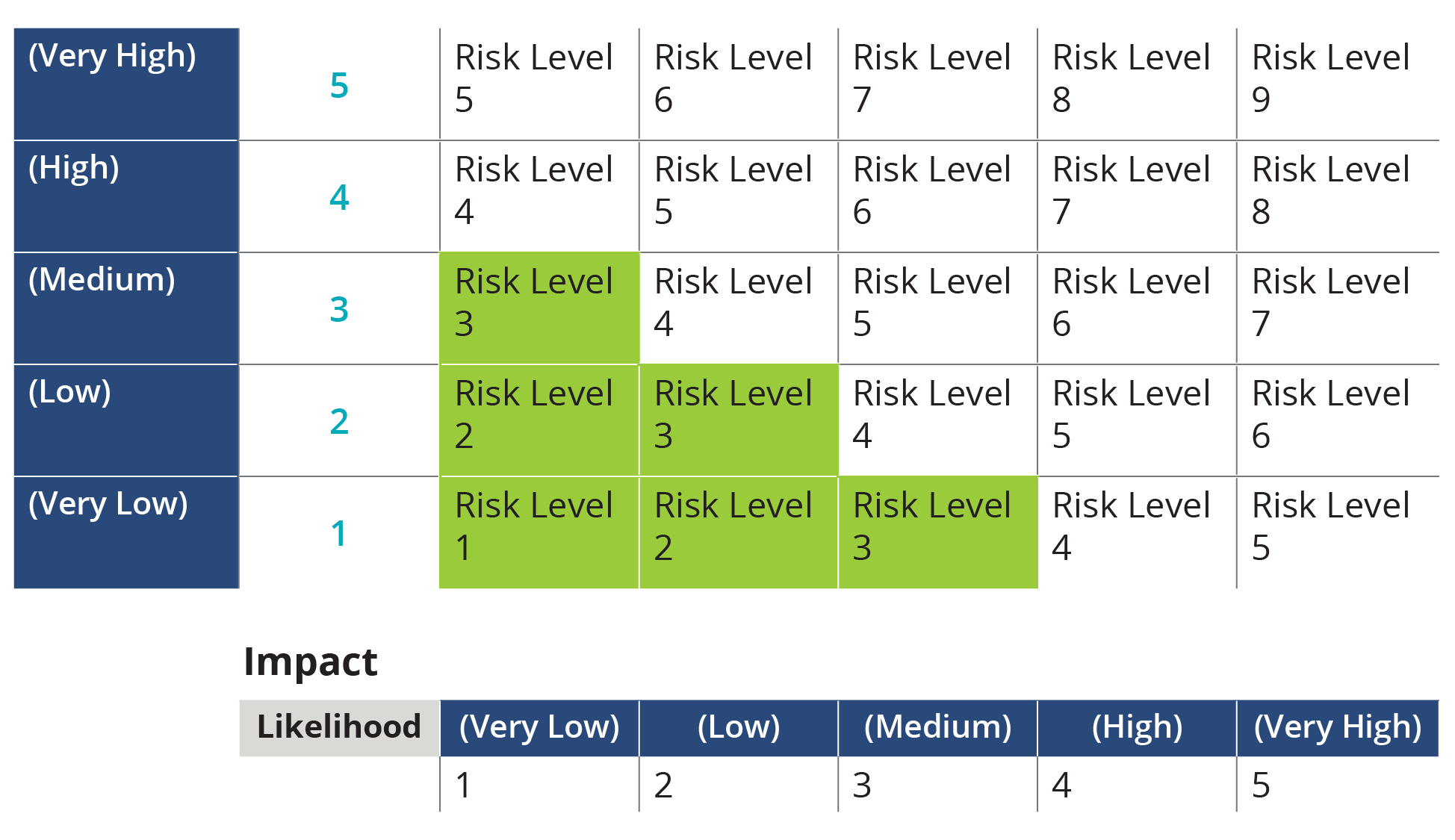
Figure 1: Sample Risk ScaleRisk assessment tools should include compatible and integral asset databases. Assets include information, data, people, third parties, hardware and software that can be categorized by asset type and asset owners. Remember to provide reference to asset database throughout the assessment.
Identify risks
Risk identification is a time-consuming activity that involves validating the risks for each of the following:
- The asset (the value to be protected)
- The threat (which can affect the asset)
- The vulnerability (the weakness that allows the threat to affect the asset).
Threats and vulnerabilities vary. Be sure to identify the risks that compromise the confidentiality, integrity and availability of data impacting the organization. Check the existing controls to avoid unnecessary duplications of measures.
Analyze risks
Risk analysis typically involves understanding how a threat might occur, which requires you to identify a vulnerability in your assets and a threat that could exploit the vulnerability.
For each security event you identify, you should be able to assess the likelihood of a threat exploiting the vulnerability and assign it a score or value. Referring back to the risk scale, the factors influencing the impact of the threat can include human, financial, legal, regulatory, reputational and operational issues, and the likelihood factors can include frequency of occurrence, previous occurrence, current levels of security control, size of attack group and knowledge of vulnerability.
Below is the example of a risk treatment with the likelihood (LHO) and business impact (BI) as defined in the earlier steps. A final rating helps address and treat the risks in the organization.
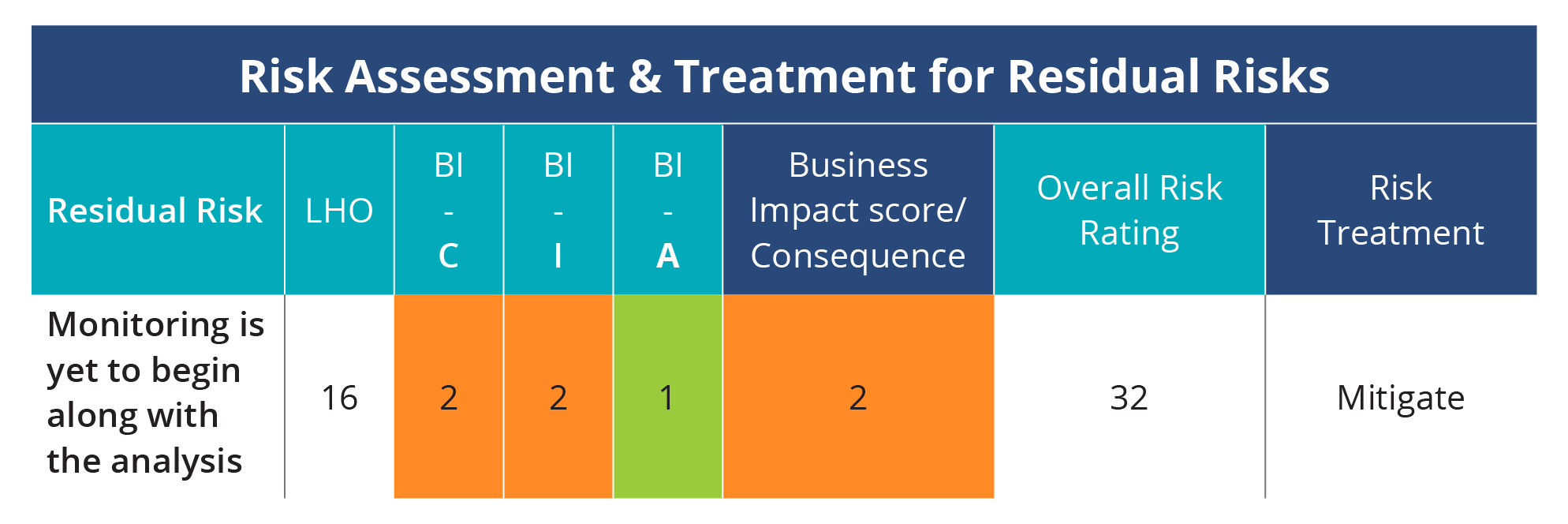
Figure 2: Risk AssessmentEvaluate risks
Your company’s risk assessment software should automatically collect the results of your risk analysis, calculate where each risk sits on the risk scale and identify whether the risk falls within your predetermined level of acceptable risk. You should quickly be able to identify your highest risks and, therefore, prioritize which risks to address first.
List risk treatment options
After evaluating and prioritizing risks, companies should respond to them based on the existing controls. Treatment options include:
- Accept the risk: This is normally done by implementing security controls that will reduce the risk’s likelihood or impact.
- Mitigate the risk: You can accept that the risk falls within your established risk acceptance criteria, or decide that it requires extraordinary decisions.
- Transfer the risk: This generally happens through insuring or outsourcing. Although your company will typically still suffer the effects of a breach, it can share the risk with someone better able to mitigate it.
- Terminate the risk: Your company can take steps to end the activity or circumstance causing the risk.
Conduct regular visits
Risk assessment is a cycle that follows the plan-do-check-act (PDCA) approach. Risks will continue to emerge, change or recede. Companies should consider all the factors documented in the first step in a risk management plan when revisiting the risk assessment on a regular basis. The results should be discussed with a company management security forum.
Information security assessments with third-party risk management
A third-party security audit can provide an independent opinion on an organization's security posture. The security auditors will verify if measures conform to generally accepted industry practices from more than 30 governmental and private organizations. This is an important activity in the continual maintenance of the information security management system.
A third-party security audit provides several key benefits, including:
- A transfer of knowledge, enabling you to better protect your people, assets and information
- A reduction of risk through the application of industry best practices
- Visibility into unknown vulnerabilities and associated risks
- Assurance that the audited entity is taking the expected steps to meet organizational and regulatory security requirements.
Internal auditing of third-party risk management becomes more effective when the two lines of defense – the security auditors and risk managers – collaborate and share information, while also leveraging each other’s abilities and tools. For instance, when risk managers maintain a centralized repository of all third-party information, security auditors can use the same system to understand the third-party risk environment and more effectively identify high-risk areas.
Conclusion
Security risk assessments help an organization strengthen its security. They can help a company identify security vulnerabilities, create new security requirements, spend cybersecurity budgets more intelligently, conduct due diligence and improve communication and decision-making. A security risk assessment can improve an organization’s security posture, which is essential in today’s increasingly insecure world.
Please fill out this form to continue.
