It has been predicted that the total number of Internet of Things (IoT) devices will grow from 11 billion today to 50 billion by 2025. Excitement and demand for IoT has grown tremendously in the last decade and is only getting stronger every year. These are smart devices that can access the internet, interact with other devices, and allow for remote management. Common examples of IoT devices are smartwatches, smart security systems, smart kitchen appliances, smart door locks and next-gen medical devices.
Unfortunately, security is not always baked into this emerging technology, and vulnerabilities abound. The severity of the vulnerabilities range from IoT devices with Mirai Botnet (a malware that exploits IoT devices) or more extreme situations like cardiac devices that are hacked to deplete battery life or threaten continuous defibrillation. Even though NIST published “800-213: IoT Device Cybersecurity Guidance for the Federal Government” in 2021, implementation of cybersecurity frameworks for IOT is quite slow.
First Steps in Securing Your IoT Infrastructure
Building Zero Trust is a good start in answering “How can I secure my infrastructure now?.” The NIST’s August 2020 publication (800-207) on Zero Trust Architecture advises implementing Zero-Trust on your non-IoT environment to secure access along with devices and identities. Operate on the simple principles of “never trust” and “verify everything.” Authenticate, check authorizations, operate on least privilege and assume that a breach will happen so you can minimize exposure.
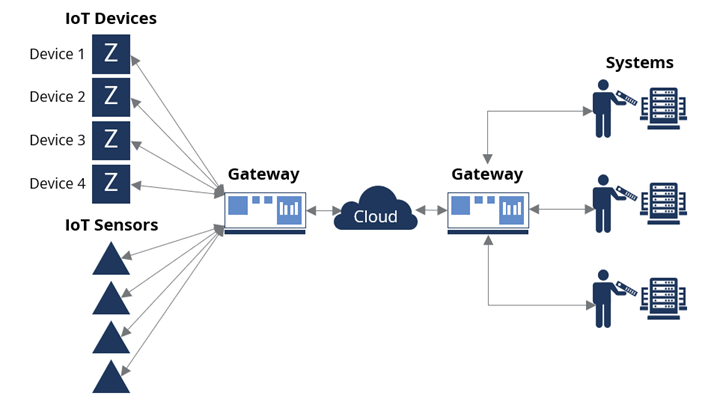
Figure 1: Typical IoT environment with connections to an internal network
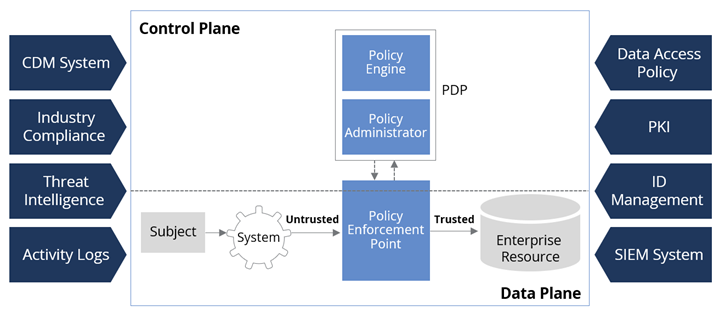
Figure 2: NIST 800-207 Zero Trust Framework
Methods for Verifying Devices and Communication
Now that you have implemented security in the non-IoT environment, carry those principles and experiences over to IoT. How do we use the principles of “never trust” and “verify everything” in the world of IoT?
Methods of verifying devices and communication include:
- Use TLS and establish trust using X.509 certificates and/or security tokens
- Re-verify and renew credentials each time the device wants to connect
- Fingerprint the device and store in an identity and device registry, if possible, to prevent rogue devices from sniffing traffic and connecting to the network
- Make sure access is based on least privilege and used on a per-session basis
- Constantly check for device upgrades, health and security configuration as most code is not written securely or updated/patched regularly
- Ensure the device is conforming to desired behaviors
- Re-verify all the above on a continuous basis
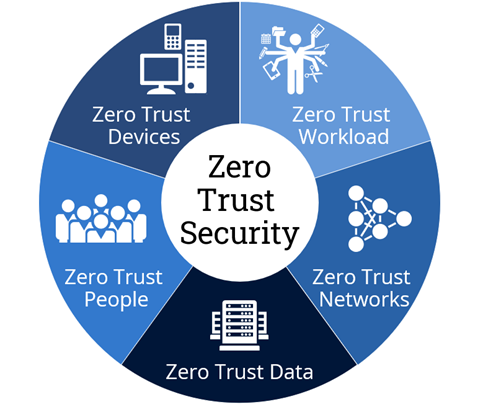
Figure 3: Zero Trust Security
IoT Security Frameworks
There are several reputable IoT security frameworks that can be applied in the application development phase of an IoT device or in post-purchase and deployment into the environment. It’s important, when researching IoT devices, that you look for ones that have incorporated a risk management framework in development. Add IoT security controls to your current risk management framework, and use in conjunction with Zero Trust principles and you will significantly decrease the attack surface a hacker can access.
IoT gives us many conveniences that we would not have had several years ago. Unfortunately, the rise of IoT happened so fast that, as in a lot of cases, securing the platform was a distant thought. Many manufacturers want to cash in on the platform and turn to security as an afterthought.
ISG researches and implements Zero Trust models for enterprises. We have the expertise to help secure your environment. Contact us to find out how we can help.
