Disinformation and deepfake AI are becoming real threats capable of compromising elections and democracy.
Microsoft’s recent acquisition of cyber threat analysis and research company Miburo is not a typical run-of-the-mill cybersecurity acquisition. Instead of focusing on security software or hardware, this acquisition helps Microsoft take advantage of intelligence and analytics in the cybersecurity market. Miburo is a data-, analytics-, intelligence- and insights-driven organization that relies on an optimal mix of proprietary tools and human expertise to identify, detect and respond to disinformation sprawl and the misuse of information. Why is this acquisition considered a cybersecurity-focused acquisition instead of a data-, analytics- or intelligence-focused one?
Why Is this a Cybersecurity Issue?
Cybersecurity offerings and innovations have evolved to protect companies and their data against malicious intent, be it a threat from the inside or the outside. This evolution can be attributed to the change in perception of how enterprises protect their IT and infrastructure assets and the rising complexity of the malicious activities of threat actors.
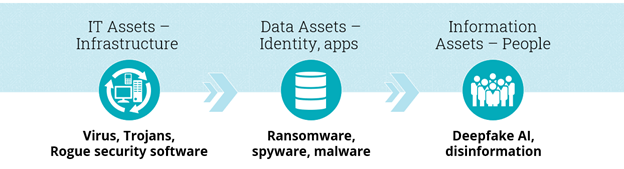
Cybersecurity’s original role was to protect IT assets such as hardware, networks and software from viruses and Trojan attacks. It gradually shifted to protecting endpoints, applications and data assets from phishing, ransomware, malware and more. Now that we are in the Information Age, companies must protect information from manipulation and prevent disinformation.
With deepfake AI and more sophisticated scamming and phishing techniques on the rise, Microsoft has been emphasizing the protection of information, which will become more relevant in the coming years. This is especially true with the growth of synthetic data and technologies such as metaverse that blur reality and the virtual world.
The keyword here is “compromise.” Microsoft wants to go farther than protecting devices, applications and identities, so it can protect “the human element” of information, in other words, the recipient. It believes misinformed citizens, individuals or groups can negatively influence elections and wars and, eventually, the whole purpose of democracy.
Reflections from 2022 ISG Provider Lens® Cybersecurity Solutions and Services
This also reflects some of the trends we have seen in this year’s cybersecurity IPL study:
- The use of analytics can help in threat and data classification to identify unknown and advanced persistent threats. There is an increase in the adoption of data-centric analytics to identify malicious behavior.
- Vendors and providers are relying on innovative approaches to determine the behavior of threats within their network, and they use contextual-awareness-based and content-based approaches to identify malicious behavior. These approaches offer increased visibility into the nature and intent of a threat so companies can isolate and further remediate them.
- There is a rise in the demand for solutions that support the correlation between intuition, intelligence, analytics and automation to drive a synergy between human expertise and machine capabilities. Service providers and vendors have started investing in human-centric solutions, where seasoned cybersecurity specialists work with advanced AI and machine learning (ML) technologies to drive real-time threat detection, isolation and response.
- Enterprises are perplexed with ransomware attacks because such attacks are aimed at exposing data or other critical assets, stealing intellectual property and misleading/misdirecting organizations and individuals to hide more advanced threats.
Microsoft’s Bet on Intelligence
Microsoft has enhanced its intelligence and proprietary analytics capabilities to identify information-based threats. This helps it better detect cyberattacks in information operations. Strong analytical capabilities can shed light on the nature and context of threats, revealing patterns that help in thwarting malicious and extremist-influenced campaigns. Contextual analyses can be integrated with other cybersecurity solutions, such as Microsoft’s cloud-native security information and event management system Sentinel to better identify the threats within enterprises and isolate intentional sabotage or individuals with malicious intentions who work with foreign information operations.
Intelligence capabilities will help enterprises identify foreign threat actors and create libraries based on behavior, language and the context of threats so their activities can be associated with malicious groups with similar intentions. This would disrupt the intended campaign, helping nations and enterprises fight against sponsored threat organizations across international borders.
Key takeaways:
- The Miburo acquisition illustrates how enterprises and economies are evolving to place higher value on information than IT infrastructure and data assets.
- Traditional security approaches are no longer relevant; enterprises require the use of behavioral, context and content analysis to detect, resolve and remediate sophisticated and advanced threats.
- An optimal combination of human expertise, machine intelligence and analytic approaches will help protect assets and identify and isolate disinformation or the misrepresentation of information with a malicious intent.
